Effective communication is vital for the success of any small business. And the right tools are just as important. But with a million and one options available, how do you choose the right ones for your business needs? This guide will help you do just that. We’ll explore the criteria for choosing the right communication… Continue reading What Are the Best Communication Tools for Small Businesses?
Author: Tom Breza
Flexible Ad Hoc IT Support in London: Expert Solutions on Demand Operum.Tech
Are you facing sporadic IT troubles in London and reluctant to invest in full-time support? Ad hoc IT support in London offers a smart, pay-as-you-need option with Operum.Tech, get the precise support your business needs, from one-time fixes to ongoing project assistance, without the commitment of a long-term contract. Key Takeaways The Perks of Ad… Continue reading Flexible Ad Hoc IT Support in London: Expert Solutions on Demand Operum.Tech
Can IT Staff Read My Emails? Exploring Workplace Privacy
The query, “Can my IT staff read my emails?” echoes across many workplaces. While a simplistic ‘yes’ might be tempting, the reality is more complex and warrants a closer look, especially in the realm of professional communication where emails often contain sensitive information. This exploration aims to shed light on who can access your emails… Continue reading Can IT Staff Read My Emails? Exploring Workplace Privacy
The Possibilities of Passkeys: A Comprehensive Guide to Password-Less Authentication
A passkey is a cryptographic key or a sequence of characters used for authentication to access a network or system. It serves as a security measure, typically in the form of a password or PIN, to verify the identity of an individual or device trying to connect to a secured environment. Passkeys offer an unparalleled… Continue reading The Possibilities of Passkeys: A Comprehensive Guide to Password-Less Authentication
12 Essential Steps to Cyber Attack Prevention: A Guide for Office Managers
Cyber attacks can cripple an organization, and as an office manager, you play an essential role in preventing these threats. But how can you stay one step ahead of cybercriminals and protect your office from potential disasters? Worry not! We’ve put together this comprehensive guide to help you navigate the world of cyber attack prevention… Continue reading 12 Essential Steps to Cyber Attack Prevention: A Guide for Office Managers
Promoting a Cyber Security Culture: An Office Manager’s Guide
As cyber threats become more commonplace, office managers need to promote a positive security culture in their workplace. This guide provides practical advice on how to do this. Engaging and training staff effectively, collaborating with the Chief Information Security Officer (CISO), and fortifying your organization’s information security posture. By following these tips outlined in “Promoting a cyber-security… Continue reading Promoting a Cyber Security Culture: An Office Manager’s Guide
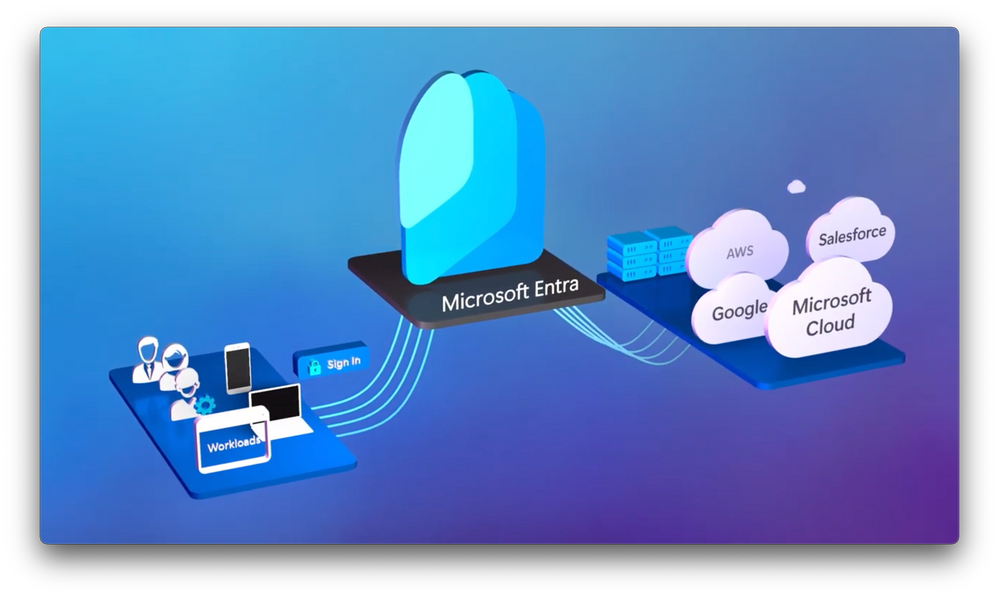
Office manager – How to manage your team computers and what is Microsoft Entra?
In the world of office managers, one has to wear many hats, from helping your team with lost delivery, trough ordering supplies to name a few, the office manager has to wear another hat, an IT hat. This is not easy and demands a lot of time and responsibility. We understand this and that is… Continue reading Office manager – How to manage your team computers and what is Microsoft Entra?
OneDrive to SharePoint – Microsoftonline: Mistakes to Avoid and What Office Managers Need to Know
Overview of Microsoft Online and OneDrive to SharePoint Microsoft Online is a collection of services and applications designed to help business owners and office managers stay organized and productive. With Microsoft 365, you’ll have access to the cloud storage you need to safely store files, create documents, and even collaborate with colleagues. OneDrive for Business… Continue reading OneDrive to SharePoint – Microsoftonline: Mistakes to Avoid and What Office Managers Need to Know
Get Professional IT Support Company in London for Your Business Needs
Choosing the best IT support company that London has to offer can be a daunting task in today’s business world. Having an experienced and reliable partner for your enterprise’s technology needs is critical for achieving growth, safety and efficiency goals. This article aims to provide helpful guidance on how to select the most appropriate provider… Continue reading Get Professional IT Support Company in London for Your Business Needs
MDM for Apple: Protecting Your Data with Microsoft Intune and Azure Active Directory (AD)
In an era where digital transformation is fueling business growth, Apple device usage, specifically Macbooks and iPhones, has become an integral part of the enterprise ecosystem. However, as these devices permeate the business environment, concerns about data protection and unauthorized access to employee devices have risen to the forefront. This is where solutions like Microsoft… Continue reading MDM for Apple: Protecting Your Data with Microsoft Intune and Azure Active Directory (AD)
How Using Active Directory can help grow your business
Today’s blog is all about Microsoft Azure Active Directory. As an IT expert with more than 20 years’ of experience in IT support services. It’s my job to keep up to date with the latest technology so you don’t have to. I love solving your IT problems as well as sharing my in-depth knowledge, and… Continue reading How Using Active Directory can help grow your business
Encryption: The Case For and Against and Why It Matters
Today’s blog is all about encryption. We’re going to talk about what encryption is, how it works, why it’s important, and more. Specifically, we’re also going to explore the great debate around encryption, whether strong, unbreakable encryption should exist, or if it should be made slightly weaker in certain situations, and why this matters for… Continue reading Encryption: The Case For and Against and Why It Matters
Incognito Mode: Who Can See What I’m Doing Online?
Today’s blog will explain how ‘Incognito Mode’ works on your web browser and explores the question of whether our online activity is ever truly private. I’ll look at the pros and cons of incognito mode using my years of experience working in IT support. Okay, first, let’s consider why we’re focusing on incognito mode today.… Continue reading Incognito Mode: Who Can See What I’m Doing Online?
Navigating the Cloud Services: Unveiling the Downsides for Businesses
Salutations to all IT aficionados and business mavens! In today’s blog, we’re heading up, up, and away into the clouds! Yes, we’re looking at the reality of cloud solutions. Specifically, how to navigate the cloud services. However, before we get started on our latest IT deep dive and go in-depth on this fascinating topic, let’s… Continue reading Navigating the Cloud Services: Unveiling the Downsides for Businesses
Top 10 Things You Should Never Do With Your Work Computer: The Never, Never List
Hello dear readers and welcome to the latest instalment of my weekly blog! As an expert IT engineer with more than two decades experience in IT support for businesses, I spend a considerable portion of my life in the digital world. Over the years, I’ve learned a few important habits to keep my digital life… Continue reading Top 10 Things You Should Never Do With Your Work Computer: The Never, Never List
Top 10 Ways To Keep Your Computer Running Smoothly
Hello there, fellow tech lovers and IT enthusiasts! Today’s topic is the top 10 ways to keep your computer running smoothly. With over 25 years of experience starting with DOS and Windows 3.11 through to Windows 11, as well as using Linux for many years AND being a keen fan of MacOS, I’ve spent countless… Continue reading Top 10 Ways To Keep Your Computer Running Smoothly
The Dangers of Deleted Data
In today’s blog, I’m going to be looking at an important topic in the field of keeping your data safe. Did you know that data you’ve deleted can be recovered by hackers? This represents a huge security risk and yet many people naturally assume that once files have been deleted, they are gone for good.… Continue reading The Dangers of Deleted Data
IT Support for Small Businesses That Want To Grow To Be a Big Business
Hello there, fellow business trailblazers! In the exciting world of small businesses, every single detail matters – from the quality of your morning coffee to the efficiency of your IT systems. Yes, you heard it right! IT support, often seen as the unsung hero in the corporate world, plays a pivotal role in your business… Continue reading IT Support for Small Businesses That Want To Grow To Be a Big Business
Stop Using Public Phone Charging Stations
Today’s blog is all about how to avoid hackers at public charging points. Ever wondered if it’s safe to plug your phone or laptop into a charging point at an airport, on a train, or in a coffee shop? Did you know you could be at risk from dangerous malware and unscrupulous hackers who want… Continue reading Stop Using Public Phone Charging Stations
Unexpected Ways Hackers Can Attack
Today’s blog is a little different, as we will be discovering ingenious techniques employed by hackers to attack security systems by using an ordinary-looking USB cable. I’m going to start by telling you a story. Our tale begins in a very non-suspicious way. USB Cable on your door-step- How Hackers Attack One ordinary day, a… Continue reading Unexpected Ways Hackers Can Attack
Building a High-Performance IT Infrastructure: The Complete Playbook – Part 2
Welcome back to part two of our complete playbook to building a high-performance IT infrastructure. First, a quick recap. Why are we doing a deep dive on this subject? And what is a high-performance IT infrastructure anyway? IT infrastructure is the collection of all the technology components needed for a business or organisation to function,… Continue reading Building a High-Performance IT Infrastructure: The Complete Playbook – Part 2
Building a High-Performance IT Infrastructure: The Complete Playbook – Part 1
In the first of a new two-part blog, I’m going to draw on my years of experience in the sector to give you a step-by-step guide on building a high-performance IT infrastructure. I call this ‘The complete playbook’ and it contains everything you need to know. First, let’s cover the basics: A: What is IT… Continue reading Building a High-Performance IT Infrastructure: The Complete Playbook – Part 1
Part Two- How To Pick The Best Laptop For Your Work
We’re back with part two of our expert’s guide to choosing the best laptop for you and your business. Why are we looking at this subject? Well, as we explained last time, in today’s fast-paced, technology-driven world, having a reliable laptop has become an essential tool for the vast majority of professionals. From handling day-to-day… Continue reading Part Two- How To Pick The Best Laptop For Your Work
Part One- How To Pick The Best Laptop For Your Work
In today’s fast-paced, technology-driven world, having a reliable laptop has become an essential tool for the vast majority of professionals. From managing day-to-day tasks to executing complex projects, your laptop is crucial in ensuring that your work is efficient, productive, and seamless. They also give you the flexibility of working on the move and out… Continue reading Part One- How To Pick The Best Laptop For Your Work
Say Goodbye to Old IT Equipment: Embrace the Digital Revolution
In this blog post, we’ll discuss the reasons why you should stop wasting money on old IT equipment and embrace the benefits of a fully digital workflow. Why You Should Say Goodbye to Printers and Scanners In today’s fast-paced digital world, it’s essential to stay up to date with the latest technological advancements. One of… Continue reading Say Goodbye to Old IT Equipment: Embrace the Digital Revolution
How to Stop Phishing: An Expert’s Guide – Part Two
Welcome back to the world of phishing. In part one of this blog, we explored what phishing is, how it works, and the many different forms it can take. Make sure you read it [Click here] and get up to speed before continuing. Today, we’re going to look at how phishing can damage your business… Continue reading How to Stop Phishing: An Expert’s Guide – Part Two
How to Stop Phishing: An Expert’s Guide – Part One
As an experienced IT expert with over 25 years in the field, I would like to help you protect yourself from one of the most damaging threats on the internet: phishing. Phishing is a type of cyberattack that uses deception to trick you into giving away your sensitive information. It can take many forms, from… Continue reading How to Stop Phishing: An Expert’s Guide – Part One
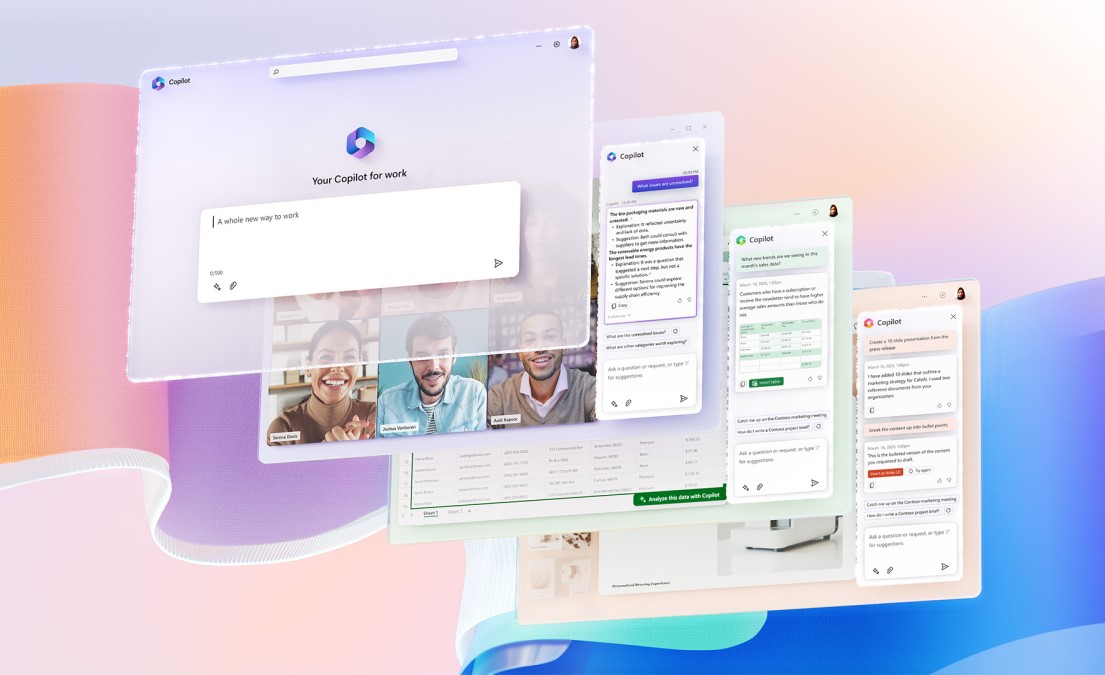
Microsoft Copilot and the Future of Managed IT Support
Today, we’re going to explore Microsoft 365 Copilot, an innovative AI-powered tool that is redefining managed IT support and the way we work. Even if you don’t work in IT, you’ll have likely seen technology like ChapGPT and Copilot being talked about in the mainstream press. As Artificial Intelligence (AI) continues to evolve, tools like… Continue reading Microsoft Copilot and the Future of Managed IT Support
Managed IT Services vs. Traditional IT Services: Which is best?
In today’s blog we’re going to look at a topic that’s particularly close to my heart. Managed IT Services vs. Traditional IT Services. We’ll explore what these terms really mean, what the difference is between them, and crucially, which one is right for your business. The contemporary business landscape has been transformed by technology. Companies… Continue reading Managed IT Services vs. Traditional IT Services: Which is best?
Confidential Emails: A Treasure Trove for Hackers
In today’s digital age, an email is an essential tool for communication and collaboration in both personal and business settings. However, email is also a treasure trove for hackers, who can use it to gain access to sensitive information and defraud individuals and businesses. In this blog, we will discuss the risks associated with email… Continue reading Confidential Emails: A Treasure Trove for Hackers
Cyber Security: Why You Need To Prioritise It During Cost-of-Living Crisis
In today’s increasingly digital world, cyber threats have become a major concern for businesses of all sizes. Cybercriminals are always on the lookout for their next target and the consequences can be disastrous. However, for small businesses, the stakes are particularly high as they often lack the resources and expertise to effectively protect themselves against… Continue reading Cyber Security: Why You Need To Prioritise It During Cost-of-Living Crisis
Public WiFi: The Essential Guide.
From online banking and shopping to social networking and streaming entertainment, the internet has become an essential part of our daily lives. We rely on the internet for a vast range of business and leisure activities. However, alongside the many benefits, there are also clear and present dangers to be aware of. In particular, the… Continue reading Public WiFi: The Essential Guide.
IT Office Relocation
Planning, Preparation and Execution One of the most critical pieces of advice for any office relocation is to plan in advance. This means creating a comprehensive timeline, identifying key milestones, and ensuring that you have the resources and support you need to execute your plan. Failure to do so can lead to costly delays, lost… Continue reading IT Office Relocation
Using a Secure VPN: An Expert’s Guide
The internet is an indispensable tool and has become an integral part of our daily lives. However, with its growing importance comes the very real need to stay safe online and keep your information secure. As an IT expert, I understand the importance of safeguarding your data and maintaining online anonymity. Every time we go… Continue reading Using a Secure VPN: An Expert’s Guide
Bypassing Multi-Factor Authentication: Discover How Hackers Operate
Explore the ways hackers evade 2FA and MFA (multi-factor authentication) and provide tips to protect yourself from online attacks
Hardware Security Keys- Pros and Cons
Read about Pros and Cons of Utilizing Hardware Security Keys as an extra layer of protection
Phishing Attacks – Cyber Crime on Another Level
Read about sophisticated phishing type of Multi Persona Impersonation and how cyber criminals are bypassing Multifactor Authentication
8 Crucial Cyber Security Tips: How Not To Get Hacked
Tips on how you can stay safe online. Facts about cybersecurity and steps to take to keep your financial data and personal information secure.
IT Boss Running 12 Races in 12 Months For Charity
IT Boss of Operum.Tech running 12 races in 12 moths to raise money for charity
We’ve launched an IT newsletter!
Join our newly launched newsletter to learn about latest IT news and in-depth features, to ‘how to’ guides for solving common problems
Cyber Security: The Essential Guide
Safeguard your business from Cyber Crime using latest technology. To understand Cyber Security, click here for more.
Dropbox for business
If you need to share files at work and security is a concern, then Dropbox for business is a great solution. Click here for more.
Cryptolocker malware
Learn about cryptolocker-malware – understand how to protect yourself from cyber threats. Click here for more.
Password security: How secure is yours?
Learn about password security – understand how to protect yourself from cyber threats. Click here for more.
A new type of phishing attack
Learn about a new sophisticated phishing attack – understand how to spot it and don’t be a victim! Click here for more.