
In today’s digital age, an email is an essential tool for communication and collaboration in both personal and business settings. However, email is also a treasure trove for hackers, who can use it to gain access to sensitive information and defraud individuals and businesses. In this blog, we will discuss the risks associated with email and how to protect yourself and your business.
Have you recently searched through your mailbox? Perhaps you were looking for an email you’ve misplaced. While you can use search terms to find old emails, it can sometimes feel like looking for needle in a haystack if it’s been a while since you had a clear-out.
Okay, let’s start with a little email housekeeping 101 to help you out. First, check what is the oldest message you have. I bet you will be surprised. In many instances, you will have more than a decade’s worth of emails. Next question is how many mailboxes do you have that contain your personal or business data? Do you have a gmail.com account, a hotmail.com, TalkTalk, BT, or another email provider? Each account can contain different sides of your digital life, some might even contain very confidential info about you, your business, or your family. The more emails you have in your mailbox, the more accounts you with different providers, and the more information you have sitting there, the greater the potential risk.
How can we deal with our email to keep our mailboxes under control and ensure they’re not a ticking time bomb that can leave us exposed to hackers and other criminals who could ruin our lives not only financially but our reputation and business too? I know this all sounds very scary, but we’re not exaggerating or trying to frighten you. Emails really are a treasure trove for hackers and it’s vital to look at your own inbox with the mindset of a cyber-criminal or, as we call them in the industry, a ‘Thread Actor’.
Thankfully, there are several ways you can protect yourself (and your inbox) and we’re going to tell you right now.
Okay, let’s get started. First, log into your email. Next, I want you to search your inbox for confidential information that you may have accidentally left undeleted in an old email.
How to find confidential info inside emails
Use the search tool in your mailbox to look for the following phrases in your emails:
- Password
- Passwords
- Username
- Confidential
- Credit card
- Debit card
Additionally, you can run a search for the following names of credit/debit card providers and the bank card numbers they commonly use:
- For Barclays Bank Search for 4659
- For HSBC Bank Search for 4543
- For Lloyds Bank Search for 4929
- For NatWest Bank Search for 4658
- For Royal Bank of Scotland Search for 4462
- For Santander UK Search for 4695
- For Monzo UK Search for 5355
- For Starling Search for 4679
In the US, you can search for bank details such as the following:
- For Chase Search for 4147
- For Bank of America Search for 4353
- For Citibank Search for 4383
- For Capital One Search for 5491
- For Wells Fargo Search for 4147
Now, what happens if during your search you have found emails containing copies of your passwords, usernames, links to documents, credit card numbers, bank statements etc. What should you do next?
My strong recommendation would be to delete all the messages. If you found that at some point you sent anyone your credit card number via email and that it is still valid, please contact the receiver of your message and ask them to check if they still have your email and ask them to delete it from their records. You should delete your copy of the message as well.
Before deleting any work emails always consult with your manager if you are dealing with company data. However, there is no good reason to keep such info inside a mailbox as it is not a safe place for such information.
What about confidential files sent as attachments?
Sharing files via email was once one of the most common ways of exchanging documents and other information with external contacts. Since it was so convenient, it became a prolific way of sharing files even you were just sending information to a colleague sat across from you. This caused over time a massive headache for IT teams as well as end users as the average size of mailboxes ballooned, and Outlook would turn from fast and furious to slow and slower. However, even less pleased was the cyber security team, as files stay inside emails forever, which creates a massive headache for them (and you).
If someone’s mailbox is hacked, Thread Actors (or cyber criminals – however you want to call them) can extract any confidential files. Imagine a company being hacked where you have sent your financial details for approval of a loan. This could include your P&L, references, copies of your ID, passport, your signature, contracts that are under NDA with a hefty price if they are released etc. The list goes on and on. Even if your own company is secure, if you send this kind of information to an external contact and their mailbox is hacked, your information and data could be out there on the internet.
Unfortunately, there is no easy way to un-send files that were sent in the past. This is a risk we must live with. There are steps you can take to protect yourself, however. Where possible, you should remove attachments from sent items in your own mailboxes if the documents are confidential. Don’t just leave those emails and files sitting in your sent items where they could be hacked. This could be a quick win in terms of reducing the risk of an attack. After all, while you may not be able to control how other people police their mailbox, but you can take care of your own housekeeping to ensure you’re as secure as possible.
Different methods to protect our digital lives
Want to shared files without attaching the document to an email? There are ways to do this that are much more secure, such as OneDrive, WeTransfer, and other secure file transfer services. Each of these has their own steps to follow but follow a similar process. Let’s look at OneDrive as an example.
How to send a link to a file located in OneDrive
First, upload your file(s) to OneDrive, then you can share a single file, or if you have more than one file, you can share a folder.
I will show you how to create the link from the web interface.
1. Open the website https://portal.office.com/
2. Click on the left top corner where you have a grid of 3×3 dots
3. Click on OneDrive
4. Navigate to the folder or file you want to share.
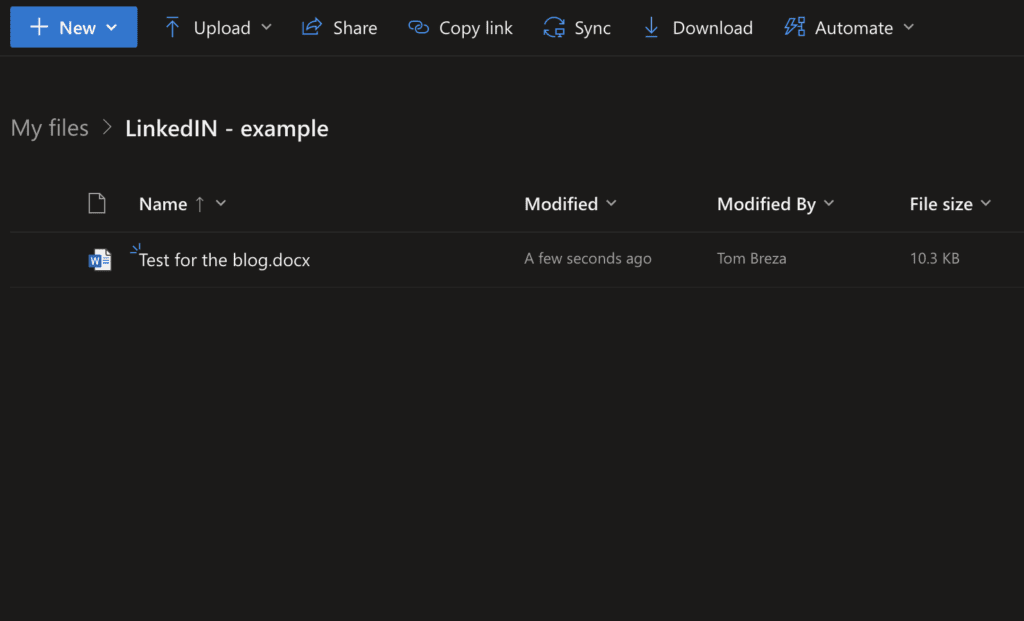
5. Click on the arrow next to the name of the file
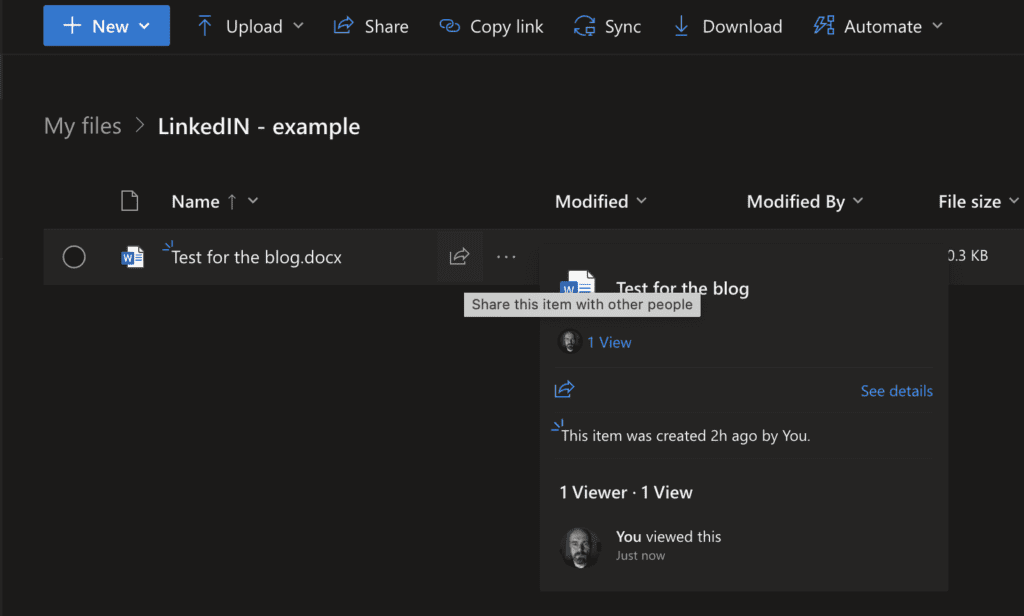
6. On the ‘Send Link’ window we can add the email address of the person who we want to share the file with
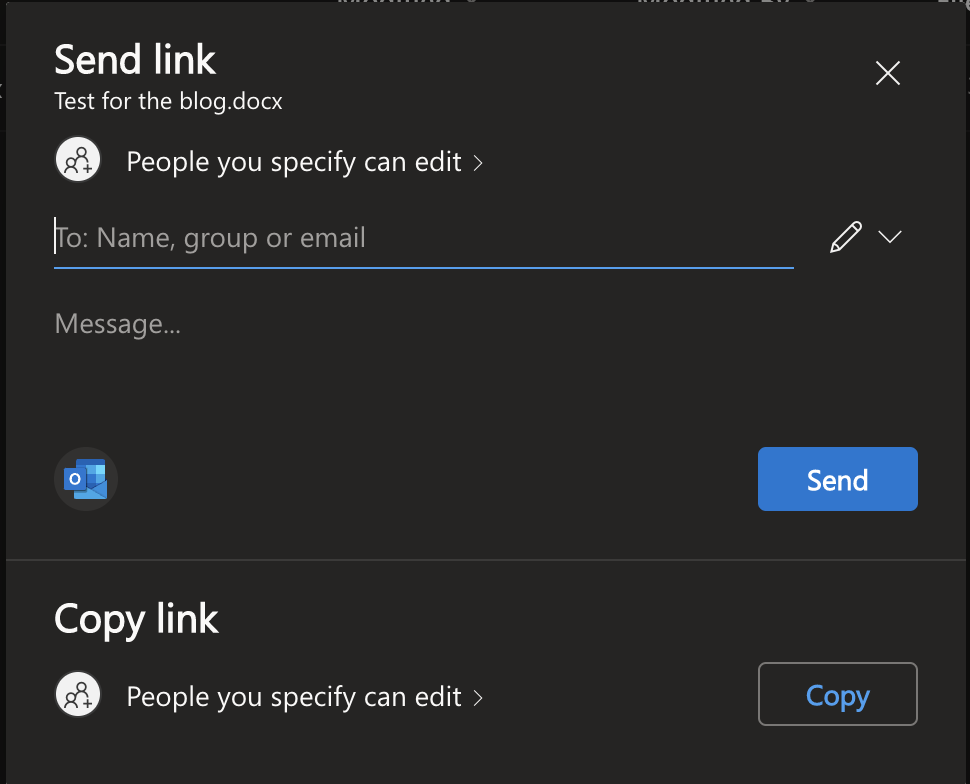
Alternatively, you can copy the link and then share it by pasting it into a composed email or via other means.
What should I do if I find old emails containing usernames and passwords?
First, let’s look back at the search we did at the start of this blog. This should reveal any old emails with a username and password in your mailbox. They could be yours; they could be another person’s, but one thing that’s certain is that they are a risk. Make sure you search all email folders and mailbox and not just your inbox as your sent items and many other sections of your mailbox are likely to include emails containing important data. My recommendation would be to delete all such emails. This is especially important to do if your emails contain multiple replies back and forward in a thread email which creates numerous copies of the credentials. This can lead to someone seeing information, such as a username or password, that you didn’t intend to share this data with simply because they’ve been added into an existing thread. As you can see, this is another reason NOT to send a username and password in such a way, or keep that information saved on an email.
How can I safely share my login details?
At some point, we will have a situation where we need to share our email credentials or Online Service Credentials with someone else, whether this is a colleague at the next desk or someone who is half a world away. How should we do it?
Here are Operum.Tech, we specialise in helping our customers protect themselves and their businesses from online and digital threats. We have a range of technology at our disposal including an innovative system for confidential or sensitive communications, which sounds like something out of a James Bond movie – the self-destructing note.
Yes, that’s right. Our customers and our team use a self-destructing note which can be found here: https://operum.tech/note/
However, not everyone has access to our system, so what should you do? The easiest thing to do would be to work with us of course! We’ll have more on how you can contact us below.
Alongside this, there are other third-party alternatives you could use, one is called https://privnote.org/
Of course, your next question is: how does this technology work? Read on to find out.
How do the self-destructing notes work?
When you open the website https://privnote.org, you can type your confidential note then just click “create note”
This will create a self-destructing note with a unique address, in our case the unique part is 5Q86QR9P4S
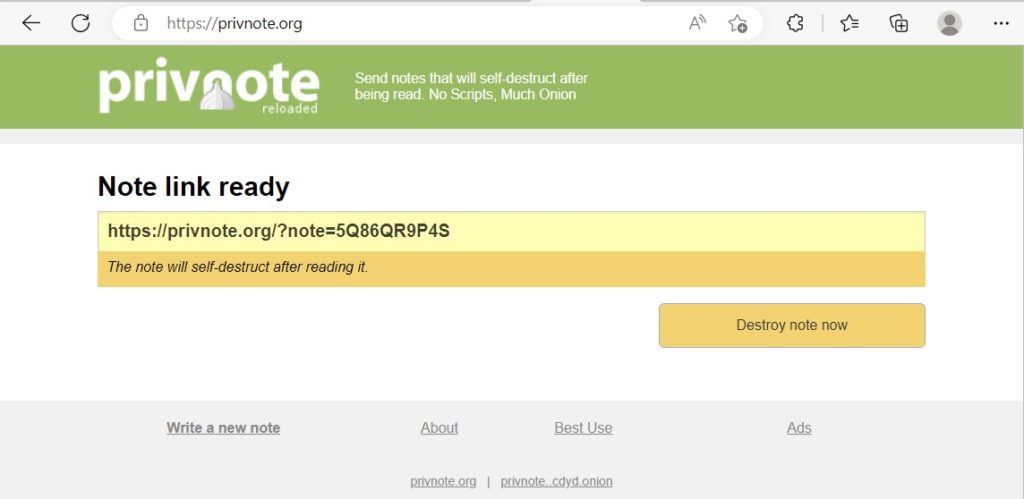
Once the note has been opened, it will be destroyed. It can’t be saved and accidentally forgotten about so it’s important to use the information (such as a password) before it is deleted.
If this is, however, the first time you try to open it you should see this:
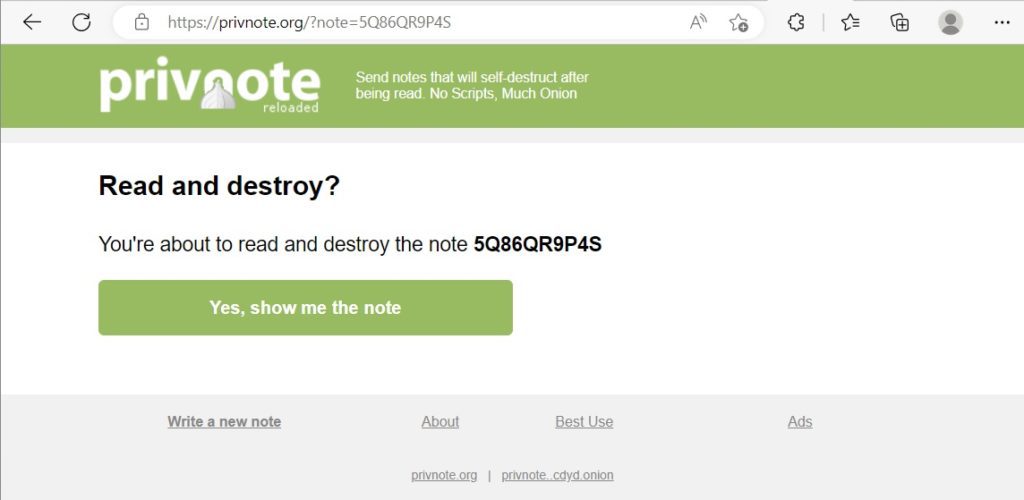
Once the note is open, you should make sure you saved the confidential info elsewhere. The next time you try to open it, you should see this:
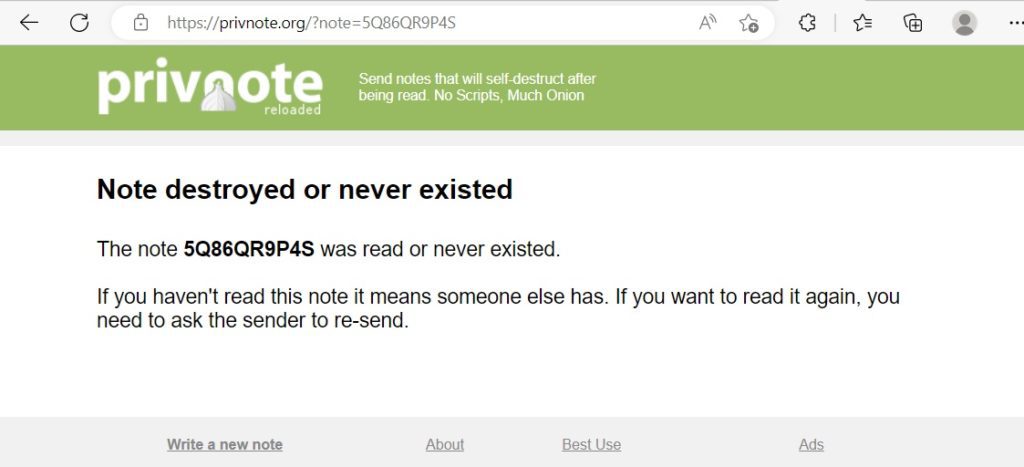
What if you try to open it the first time and you get the message that the note is destroyed?
This could indicate that an unauthorised person accessed the note, and that the contents are no longer confidential. In such a situation, it would be advisable to act fast and reset the password asap.
Now, there are several important caveats to bear in mind when using this technology. Our advice would be to never put all the details of an account inside a single self-destructing note.
For example, never send the username, password, account details, or other credentials together. Instead, send each part separately. Why? If, for any reason, someone unauthorised managed to access the content, if they only have a password (ideally a random string of numbers, letters, and symbols) they will have no username to go with it and no clue what accounts it refers to. It is effectively like giving someone one piece of a puzzle instead of all the pieces.
A potential attacker will find it much harder to work out how to use the information. The only exception would be if they had also hacked your email account, which is another reason to keep your mailboxes secure and clutter-free by taking care of your digital housekeeping and following security advice.
It is worth remembering that a mailbox is an absolute treasure trove of personal interactions and data that can be used to defraud individuals and businesses. They can use personal information obtained from email interactions to make the fraud appear more convincing. To avoid this risk, you should be wary of any requests for personal or financial information, even from seemingly trusted sources, and always verify the identity of the sender before sharing any sensitive information.
How can I protect myself?
In addition to the above measures, there are several other ways to protect yourself and your business from email-related risks:
- Use MFA or Hardware Key: Multi-factor authentication (MFA) and hardware keys provide an additional layer of security by requiring the user to provide more than one form of authentication. MFA requires the user to provide a password and a code sent to their phone or email address, while hardware keys are physical devices that must be plugged into the computer to access sensitive data. However, it is important to avoid using SMS to authenticate, as it can be easily compromised.
- Use services such as Operum.Tech and get support from the experts. With two decades of experience, Operum.Tech provide IT support in London including additional security and guidance to protect your business from email-related risks. IT support services like Operum.Tech can provide advice on best practices for email security, assist with setting up secure ways to transfer files, and monitor for potential security breaches. Additionally, we can provide training for employees to help them identify and avoid email-related risks. To find out more click here.
- Remain cautious with personal and financial information. Always verify the identity of the sender before sharing any sensitive information.
- Equally, be wary and cautious about any strange requests via email such as sharing passwords or credit card details. In other words, anything that doesn’t feel right. Ask yourself, would your customer, boss, or colleague really ask you to do this? If you have doubts STOP. Talk to another person, a colleague, a manager, a friend, a spouse. It’s always better to be safe than sorry.
- Regularly update software and security measures. By ensuring that all software and security measures are up to date, you can minimize the risk of a data breach.
Conclusion
As we’ve discovered, emails can a literal treasure trove of data for hackers if we send or save sensitive information or confidential files via our inbox and forget to delete. A little housekeeping can go a long way to help, but it’s also important to follow best practice in terms of email security and to get advice from the experts, such as the friendly team here at Operum.Tech. There are lots of ways we can help you protect yourself and ensure your mailbox is more like a safe and secure bank vault than a treasure chest for potential criminals.
If you’re worried that your IT security isn’t as strong as it could or should be at your place of work and you’re not sure how to start when it comes to remedying this, send us an email or click on the contact us button below. Our friendly team of experts will handle your request professionally and confidentially, drawing on years of experience. There’s genuinely no such thing as a bad question to ask and no problem that’s too big or too small. We deal with many customers who are not IT pros who find it difficult to deal with the latest technology and security challenges. That’s where we come in. We’ve spent more than 25 years learning and perfecting everything we know in the field of IT, and we are here to help. You will find that our team is not only professional but polite, friendly, and keen to lend a hand. Contact us.
Bonus FAQ:
Q: How can I prevent hackers from accessing my email account?
A: Use strong passwords and enable two-factor authentication. Avoid using public Wi-Fi to access your email account and be cautious of phishing emails and suspicious links.
Q: Is it safe to send sensitive information via email?
A: No, it is not recommended to send sensitive information such as usernames, passwords, or financial information via email. Instead, use secure file transfer services or self-destructing notes to share sensitive information.
Q: Can IT support services help protect my business from email-related risks?
A: Yes, IT support services such as Operum.Tech in London can provide additional security and guidance to protect your business from email-related risks. They can also assist with setting up secure file transfer services and implementing best practices for email security. Click here for our services.
Sign up below to join the Operum newsletter



