- Share on
-
-
-
Hand-picked related articles
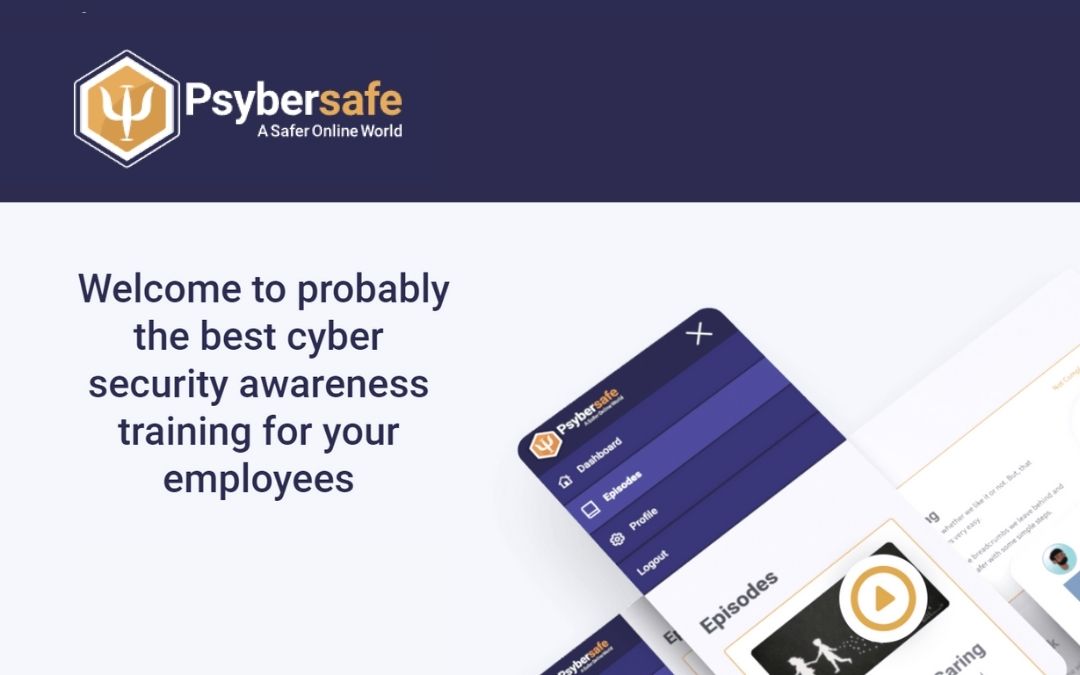
A Modern Take On Cyber Security Awareness With Psybersafe.com
I came across the online portal Psybersafe.com which helps with cyber security awareness and had a chat with its creator Mark Brown. Mark kindly allow us to test-ride their product and share our experience. In Mark’s words, their platform is a tool that will help with security awareness for businesses over many years. The platform… Continue reading A Modern Take On Cyber Security Awareness With Psybersafe.com
- Publish date
- August 2, 2023
- Topic
- Category: Cyber Security

Promoting a Cyber Security Culture: An Office Manager’s Guide
As cyber threats become more commonplace, office managers need to promote a positive security culture in their workplace. This guide provides practical advice on how to do this. Engaging and training staff effectively, collaborating with the Chief Information Security Officer (CISO), and fortifying your organization’s information security posture. By following these tips outlined in “Promoting a cyber-security… Continue reading Promoting a Cyber Security Culture: An Office Manager’s Guide
- Publish date
- August 22, 2023
- Topic
- Category: Cyber Security

IT Support for Small Businesses That Want To Grow To Be a Big Business
Hello there, fellow business trailblazers! In the exciting world of small businesses, every single detail matters – from the quality of your morning coffee to the efficiency of your IT systems. Yes, you heard it right! IT support, often seen as the unsung hero in the corporate world, plays a pivotal role in your business… Continue reading IT Support for Small Businesses That Want To Grow To Be a Big Business
- Publish date
- May 22, 2023
- Topic
- Category: IT Support
