Addressing a Common Concern
As CEOs, we often grapple with decisions about technology, even if we’re not tech experts. A common query we encounter from our clients is about Wi-Fi security: should guests be allowed access to your office Wi-Fi, and if so, how should this be managed? This CEO’s guide to Wi-Fi Security. is specifically crafted to offer clear, actionable advice, enabling you to make well-informed decisions that safeguard your company’s digital integrity. We understand the challenges that come with such decisions, and our goal is to provide you with practical insights to address them confidently.
Understanding the Risks of Shared Wi-Fi Access
1. Persistent Access: A Hidden Vulnerability
Allowing visitors to access your main Wi-Fi network can lead to a significant security gap. This is akin to giving someone a key to your office: once they have it, they can potentially re-enter anytime, posing a risk long after their initial visit.
2. Compromised Devices: An Internal Threat
If a visitor’s device harbours malware, connecting it to your main Wi-Fi could inadvertently introduce a cyber threat to your network. Such devices can act as a gateway for cybercriminals to infiltrate and exploit your network.
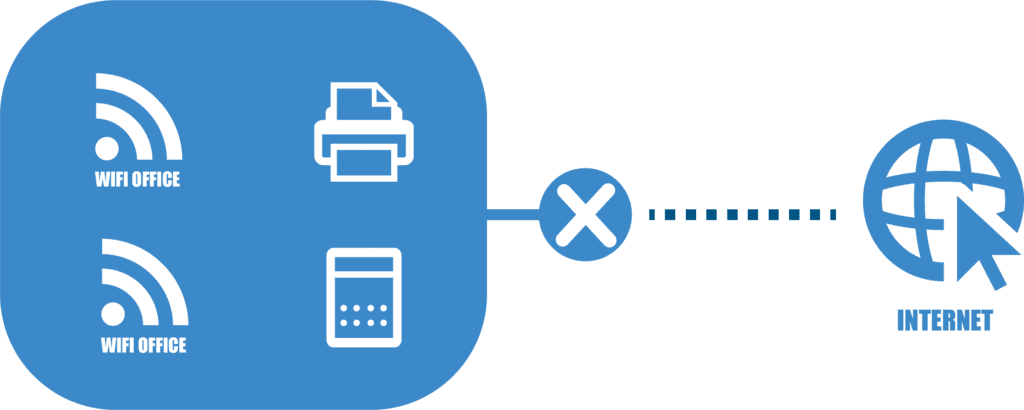
The Solution: Implementing a Guest Wi-Fi Network
A separate Wi-Fi network for visitors safeguards your main corporate network from external threats. This dedicated guest network isolates visitor devices, ensuring they don’t have access to critical company data or operations. Furthermore, the beauty of this approach is that you can change the password for the guest network as often as you wish without causing any inconvenience with reconnecting devices to your main office Wi-Fi. This flexibility enhances your security measures without disrupting the workflow or connectivity of your internal operations.
Advantages of a Dedicated Guest Network:
- Enhanced Security: Keeps your primary network secure from external devices.
- Controlled Access: Allows you to manage guest network usage effectively.
- Ease of Management: Simplifies administrative tasks like password updates.
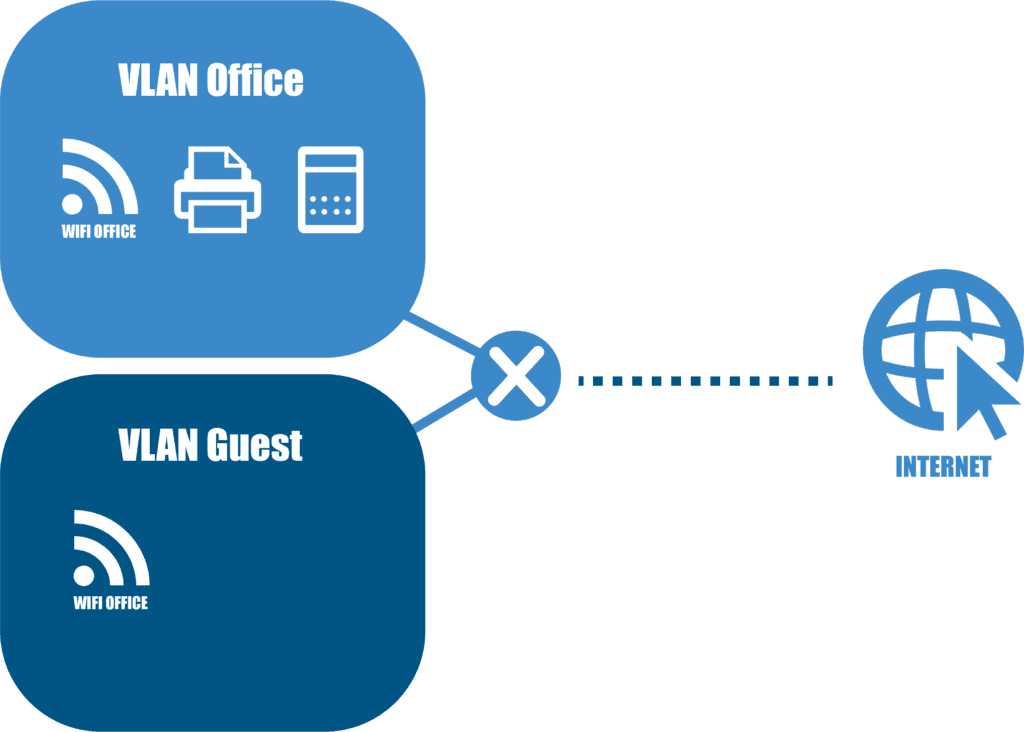
Introducing VLANs for Robust Security
Using VLANs (Virtual Local Area Networks) for your guest Wi-Fi adds an extra layer of security. To understand VLANs, imagine your Wi-Fi without VLAN as a house with two doors entering the same room. Both your company’s devices and guests’ devices share this space. However, implementing VLANs is like creating two separate rooms within the same house. One room is exclusively for your company’s devices, and the other is solely for guests. The only shared aspect is the internet connection itself. This segregation ensures that even if guests are on your physical network, they remain in a separate, virtual segment, unable to access your main network.
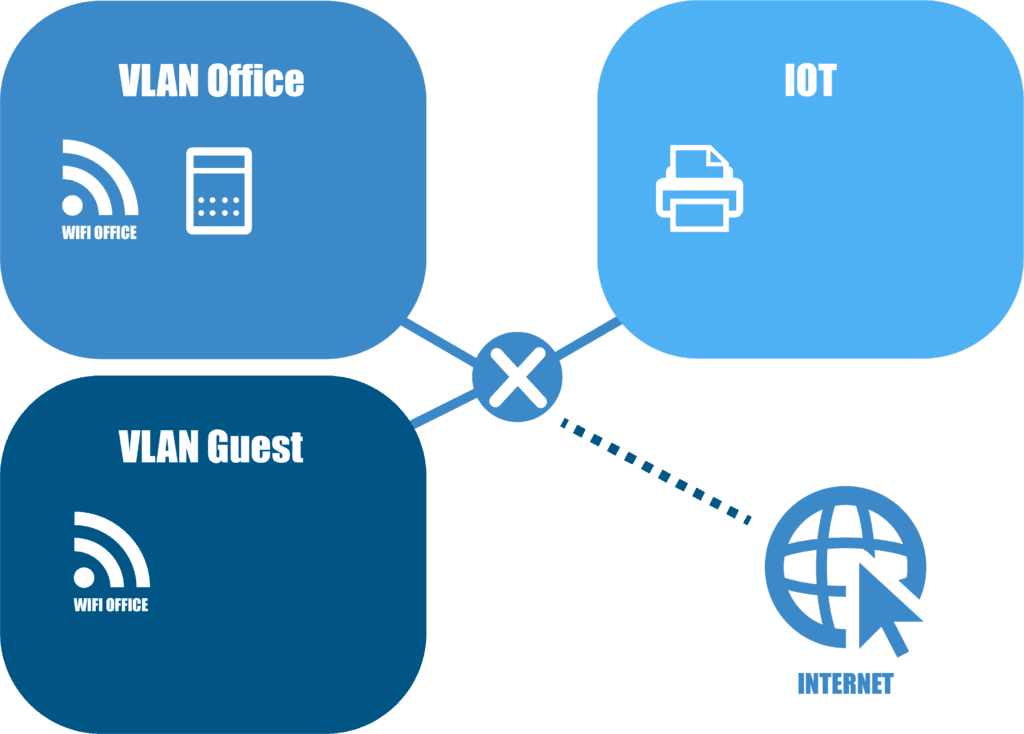
Smart Device Segregation
In our increasingly interconnected world shaped by the Internet of Things (IoT), it’s crucial to implement a practice known as Smart Device Segregation. This involves assigning devices such as smart TVs and printers to a dedicated network separate from your primary Wi-Fi infrastructure. This strategic separation serves multiple purposes. Firstly, it significantly diminishes the necessity for frequent password changes on your main Wi-Fi network, as these changes typically disrupt the connectivity of numerous devices. By isolating smart devices on a distinct network, any alterations to their passwords won’t impact the primary network’s operational stability.
Moreover, this segregation acts as a security measure, reducing the potential risks associated with smart devices. Smart TVs and printers may have inherent vulnerabilities that could be exploited by malicious entities. By placing them on a separate network, you create an additional layer of defence, isolating these devices from critical company data and operations.
Secure Authentication for Main Wi-Fi
To fortify the security of your main Wi-Fi network, employ a robust and secure authentication method aligned with your company’s internal login credentials. This ensures that only authorized personnel with the appropriate credentials can gain access to the network. Implementing secure authentication not only guards against unauthorized access but also enhances the overall cybersecurity posture of your organization. By aligning Wi-Fi access with internal login credentials, you establish a consistent and reliable approach to network security, reducing the risk of unauthorized entry and potential data breaches.
Conclusion
As a CEO, the responsibility of protecting your company’s digital assets is paramount. By adopting these Wi-Fi security measures, you can significantly fortify your company’s digital defences. Remember, proactive steps in digital security are crucial for safeguarding your business in the ever-evolving cyber landscape.
If you need a helping hand with your Wifi Security, simply send us a message at [email protected] or call us on 0800 389 6798. Our IT support services for businesses include everything from cyber security, cloud computing, and IT compliance to IT infrastructure support, cyber essentials, IT office relocation, and more. We love working with our IT support clients and using our IT knowledge and experience to make their lives easier. We take care of the tech stuff so you can focus on what you do best. You can contact us by clicking here.
Sign up below to join the Operum newsletter