
Let’s start with the important bit. If you’re on this page because a someone has lost a laptop, here’s what you do:
- Report the loss to your IT department and to management. Both need to know.
- If you have another way onto your network account (another laptop, for example), go in and change your password
- Hopefully your IT department can remotely access your device to lock it, reset passwords and remotely wipe all data from the device. Something like Microsoft Intune is ideal.
- Assuming Find My Device (if you have a Windows device) is switched on, you have a good chance of tracking it down.
Hopefully now the device has been secured, you can read on about why it is vital you can do this when a laptop (or other device) is lost.
Mobile working adds risk of devices being lost
The shift towards a mobile-centric workplace has brought with it a heightened risk of lost or stolen devices. Addressing this challenge requires not just a reaction plan, but a proactive strategy. This blog post delves into the necessity of setting up solutions like Microsoft Intune in advance, enabling control over devices and ensuring the ability to wipe data remotely if needed. Aimed at CEOs and Office Managers, we’ll explore how foresight in implementing these measures can protect your business from the risks associated with losing laptops.
Planning in advance
A lost or stolen laptop is a serious threat to your business and your reputation. Just look at how quickly it hits the news when a government minister loses a device. If this happens you cannot lock the door after the horse has bolted. If the ability to lock/wipe the device isn’t already in place, whatever is on the device is available to others if they can get past your password protection.
The tool we recommend to help you protect all your company devices (and to protect your network if you use contractors working on their own devices) is Microsoft Intune. It provides robust security and management of your organisation’s mobile devices. It also gives you the ability to immediately respond to device-related issues and helps prevent potential data breaches.
3 steps to device and network protection
There are three key steps needed to ensure you are protected from lost laptops and other devices. (click on the step to move down this article to that specific section):
- Device enrollment
- Making full use of Intune/Microsoft 365 security tools
- Educating your team on what they need to do when something happens
Device Enrolment
One of the key aspects of this early implementation is device enrollment. It is imperative to ensure that all company devices are enrolled in Microsoft Intune. Device enrollment is a foundational step in the overall management and security strategy for your fleet of mobile devices. By enrolling devices in Intune, you enable the application of security policies, configuration settings, and access controls, thus enhancing the overall security posture of your organization.
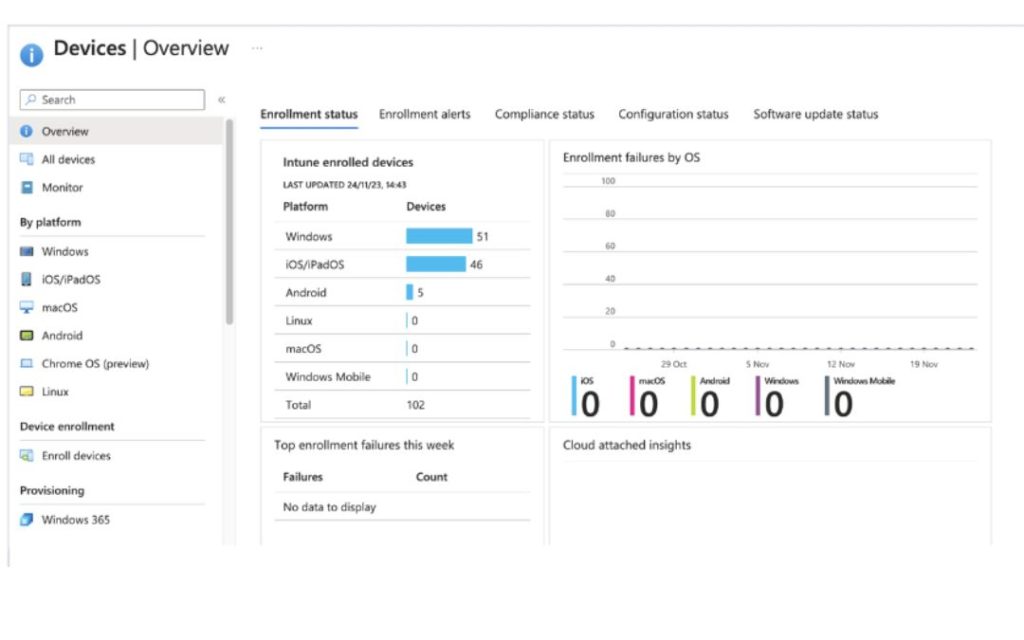
Device enrollment in Microsoft Intune provides several benefits:
- Security Measures: Enrolling devices allows you to implement security measures such as device compliance policies, conditional access, and encryption. This helps protect sensitive data and ensures that only authorized and secure devices can access corporate resources.
- Remote Management: With device enrollment, you gain the capability to remotely manage and troubleshoot devices. This is particularly crucial in scenarios where a device is lost or stolen. Intune allows you to locate, lock, or wipe a device remotely, minimizing the risk of unauthorized access to corporate data.
- Consistent Configuration: Enrolling devices in Intune ensures that they adhere to a consistent set of configuration settings and policies. This consistency is essential for maintaining a standardized and secure environment across all devices in your organization.
- Automatic App Deployment: Intune facilitates the automatic deployment of required applications to enrolled devices. This streamlines the onboarding process for new devices and ensures that essential business applications are readily available to users.
- User Productivity: A well-enrolled device ensures a seamless and productive user experience. Users can access corporate resources securely, knowing that their devices are compliant with organizational security policies.
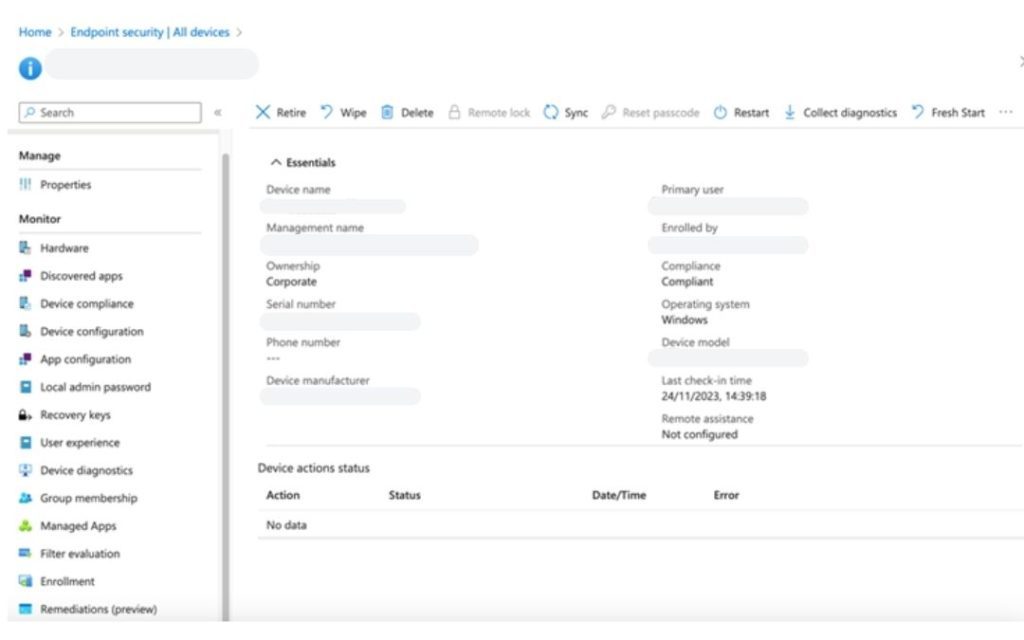
Leveraging MS Intune and Office 365:
Leveraging Microsoft Intune in conjunction with Office 365 provides a comprehensive approach to device management and security, offering a range of features to enhance control, protect sensitive data, and fortify overall defenses.
Comprehensive Device Management with MS Intune: Microsoft Intune goes beyond basic remote wiping capabilities, offering detailed control over devices within an organization. This includes the ability to implement a wide array of security policies tailored to meet specific organizational needs. These policies may cover aspects such as device compliance, application management, and network access controls.
Enhancing Security with Office 365: When combined with Office 365, Microsoft Intune’s capabilities synergize with the security features inherent in the Office suite, resulting in a powerful defense mechanism.
- Encryption: Office 365 offers robust encryption features, securing data both in transit and at rest. By leveraging these encryption capabilities alongside Intune, organizations can ensure that sensitive information remains protected on devices and during data transfer.
- Multi-Factor Authentication (MFA): Office 365 supports MFA, adding an additional layer of security beyond traditional username and password authentication. When integrated with Intune, MFA further fortifies the authentication process for devices, reducing the risk of unauthorized access even if login credentials are compromised.
- Conditional Access: Combining Intune and Office 365 allows organizations to implement conditional access policies. This means that access to Office 365 resources can be dynamically granted or denied based on the compliance status of the device. For instance, only devices that meet specific security criteria, as defined by Intune policies, may be allowed to access sensitive Office 365 data.
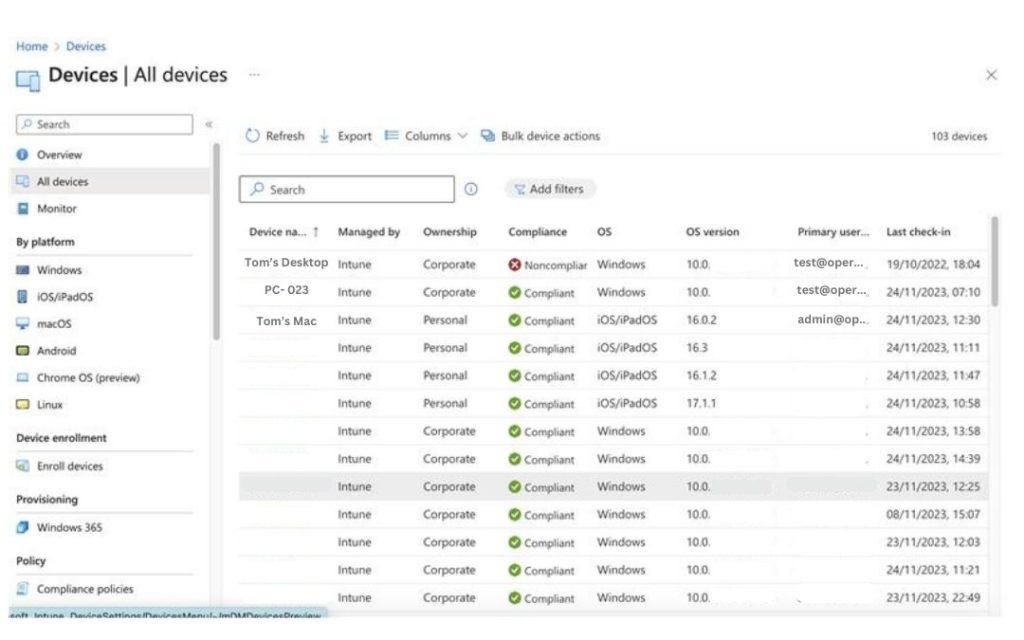
The Role of Managed IT Support:
- Expertise in Setup and Management: A service like Operum.Tech can assist in the initial setup of MS Intune, ensuring all devices are correctly enrolled and managed.
- Training and Preparedness: Regular training sessions provided by IT support partners can keep your staff informed and prepared for potential device loss scenarios.
- Swift and Efficient Response: In the event of a lost laptop, having a skilled IT support team ensures a rapid and effective response, minimizing potential data exposure.
If you’re not getting the support you need from your current IT provision, we’d love to have a chat. Click here to get in touch.
Proactive Security Culture:
- Fostering Awareness: Educate your team about the importance of security in a mobile-dominated workplace.
- Regular Policy Reviews: Keep your device and data security policies up-to-date and ensure they are well communicated and adhered to.
- Backup and Data Recovery Plans: Regular data backups are essential, ensuring business continuity even when a device is irretrievable.
The mobility of work devices is a norm, proactive security measures are not just beneficial; they are necessary. Setting up and effectively managing Microsoft Intune, combined with the security strengths of Office 365 and the expertise of a managed IT service like Operum.Tech, can significantly fortify your business against the risks of lost or stolen devices. Proactivity is the key to maintaining a secure and resilient business infrastructure.
So what can you do to stay ahead?
The most important part is not to wait for a security incident to realize the importance of proactive measures. Reach out to Operum.Tech today by
and ensure your business is equipped with the right tools and strategies to handle the challenges of a mobile workforce securely. Stay ahead in protecting your business’s most valuable assets.
Sign up below to join the Operum newsletter



